Despite the great success achieved in face biometrics in recent decades, little attention has ever been paid on the critical problem of face antispoofing. It is now gradually aware that existing face recognition systems are vulnerable to fake face attacks. Unauthorized attackers may try to spoof the face recognition systems by exhibiting fake copies of an authorized client's face, in forms such as photos or videos. Although simple, these attacks are usually quite successful. Yet there still lack efficient anti-spoofing algorithms to solve this problem.
We are pleased to find that now researchers begin to focus on this issue, and some amazing progresses have been made. Noticeably, Idiap Institute has launched a project, named TABULA RASA, aiming to design secure and reliable biometric systems. They also held a 2D face antispoofing contest in conjunction with IJCB'11, to serve as an evaluation platform to verify different algorithms. The database has now become available, and another similar database is NUAA database published by X. Tan (ECCV'10).
Here we release another face anti-spoofing database, which has a signifcant improvement in data collection compared with previous databases. This database mainly focuses on the variation of collected data, trying to provide a comprehensive collection. Specifically,
the database contains 50 genuine subjects, and fake
faces are made from the high quality records of the genuine
faces. Three imaging qualities are considered, namely the
low quality, normal quality and high quality. Three fake
face attacks are implemented, which include warped photo
attack, cut photo attack and video attack. Therefore each
subject contains 12 videos (3 genuine and 9 fake), and the
final database contains 600 video clips. Test protocol is provided,
which consists of 7 scenarios for a thorough evaluation
from all possible aspects. A baseline algorithm is also
given for comparison, which explores the high frequency information
in the facial region to determine the liveness. We
hope such a database can serve as an evaluation platform
for future researches in the literature. For details, please refer to our ICB'12 paper [1].
Below are figures showing the overall video data for an individual subject, and the baseline performance under the 7 scenarios in the protocol.

Fig. 1. One complete video set for an individual subject.
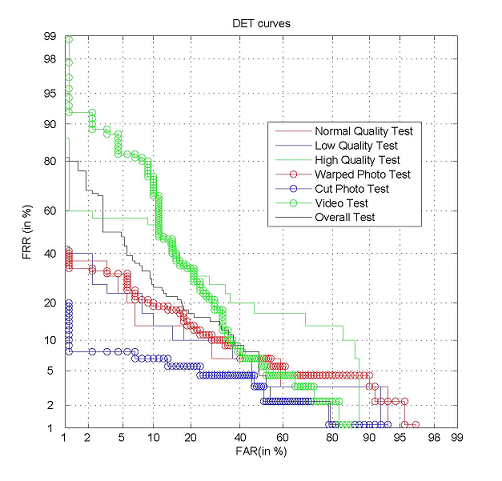
Fig. 2. Baseline performance under 7 scenarios.
Download curve data from here.
Download Instructions
To apply for the database, please follow the steps below:
- Download and print the document Agreement for using CASIA database
- Sign the agreement
- Upload the agreement to the submission website
- Check your email to find a login account and a password of our website after one day, if your application has been approved.
- Download the CASIA Face Antispoofing database from our website with the authorized account within 48 hours.
Copyright Note and Contacts
The database is released for research and educational purposes. We hold no liability for any undesirable consequences of using the database. All rights of the CASIA Face Antispoofing database are reserved. Any person or organization is not permitted to distribute, publish, copy, or disseminate this database.
References:
[1] Zhiwei Zhang, Junjie Yan, Sifei Liu, Zhen Lei, Dong Yi, Stan Z. Li. A Face Antispoofing Database with Diverse Attacks. In proceedings of the 5th IAPR International Conference on Biometrics (ICB'12), New Delhi, India, 2012.
|

